Introduction
The Widespread Vulnerability Scoring System (CVSS) has lengthy been a main methodology for precisely assessing vulnerability severity, offering a standardized strategy to speaking the traits and severity of software program vulnerabilities. With the discharge of CVSS model 4.0, vital enhancements have been made to reinforce the precision and suppleness of vulnerability scoring.
After greater than eight years for the reason that final main replace, CVSS v4.0 was formally revealed on November 1st, 2023, and has been step by step adopted by main organizations within the cybersecurity area.
Overview of CVSS v4.0
CVSS is an industry-open framework designed to speak the traits and severity of software program vulnerabilities.
Model 4 now consists of 4 metric teams:
Base Metrics
Symbolize the intrinsic qualities of a vulnerability that stay fixed over time and throughout person environments.
Environmental Metrics
Symbolize the traits of a vulnerability
distinctive to a person’s setting and should or could not
change over time.
Menace Metrics
Mirror the vulnerability traits that will change over time, specializing in the present state of exploit strategies, exploit code availability, or lively “in-the-wild” exploitation.
Supplemental Metrics
A brand new non-obligatory group that gives extra extrinsic context with out affecting the bottom rating.
The first targets of CVSS v4.0 are to enhance scoring accuracy and granularity, improve flexibility throughout totally different environments, and assist improve vulnerability prioritization capabilities.
Key Adjustments within the Newest Model
CVSS v4.0 introduces a number of vital modifications within the metrics and values to enhance the main focus and granularity of the ensuing rating. Some key modifications embrace:
Teams Adjustments
| CVSS v3.1 | CVSS v4.0 |
| Base Metrics | Base Metrics |
| Temporal Metrics | Menace Metrics |
| Environmental Metrics | Environmental Metrics |
| – | Supplemental Metrics |
New Metrics and Parameters for the Base Group
Assault Necessities (AT) metric: Assesses conditions for exploitation by evaluating situations within the weak element that allow the assault.
Assault Complexity (Clarifications): The Assault Complexity (AC) metric was improved to have a clearer which means and segregate the concepts that are actually described within the Assault Necessities (AT).
Person Interplay (UI) metric: Now presents three values (None, Passive, Energetic) to higher describe required person involvement.
Susceptible System and Subsequent System Impacts: Replaces the earlier Scope idea to focus extra on the connection between scope and impression, offering extra Impression info on each Susceptible System (VC, VI, VA) and Subsequent Methods (SC, SI, SA).
Revamped and Simplified Metrics
Menace Metrics (previously Temporal Metrics)
Displays a shift in the direction of incorporating menace intelligence in scoring. The Exploit Maturity (E) metric (previously Exploit Code Maturity) now can have 4 values: Not Outlined (X), Attacked (A), Proof-of-Idea (P), and Unreported (U).
Environmental Metrics
These metrics enable for the adjustment of the Base Rating to replicate the significance of the affected IT asset to a person’s group. The Environmental metrics group has been up to date to incorporate a Security parameter when there could possibly be an impression on people. This new parameter permits for the evaluation of potential security impacts in techniques the place security is a important concern, significantly related for OT, ICS, and IoT environments.
Supplemental Metrics
This solely new, non-obligatory group gives extra context with out affecting the bottom rating, together with:
- Security (S): Assesses security impression on human life
- Automatable (AU): Signifies if vulnerability exploitation might be reliably automated at scale
- Restoration (R): Measures system restoration capabilities post-exploitation
- Worth Density (V): Assesses the focus of priceless sources accessible via exploitation
- Vulnerability Response Effort (RE): Displays the trouble required to efficiently reply to the vulnerability
- Supplier Urgency (U): Permits distributors to point the urgency of remediation
Significance of Menace Intelligence
The renaming of Temporal Metrics to Menace Metrics emphasizes the elevated significance of menace intelligence in CVSS v4.0. This transformation acknowledges that the menace panorama is continually evolving and {that a} vulnerability’s danger stage can change quickly based mostly on menace actor conduct. Actual-time menace intelligence is essential for correct danger evaluation.
Enhancements in Severity Evaluation and Scoring
CVSS v4.0 introduces vital enhancements in severity evaluation and scoring, aiming to offer extra correct, nuanced, and context-aware vulnerability scores.
Improved Granularity
- Extra Exact Metric Values: Introduction of recent metrics and increasing current ones enable for extra exact vulnerability descriptions.
- Separation of Susceptible and Subsequent Methods: This transformation permits for extra exact scoring of the impression for vulnerabilities that have an effect on a number of techniques or have cascading results.
- Refined Assault Complexity Evaluation: The separation of Assault Complexity (AC) and Assault Necessities (AT) metrics permits for a extra nuanced analysis of the problem in exploiting a vulnerability.
Improved Scoring System Improvement
CVSS v4.0 addresses the “rating inflation” downside seen in v3.x via extra balanced severity distribution and extra exact scoring. The refined scoring system prevents too many vulnerabilities from being rated as important, addressing the notion that “most” vulnerabilities had been scored 9.8 in model 3.1.
Understanding CVSS v4.0 Rating Adjustments
To grasp how scoring has advanced, let’s take a look at the important thing metric modifications from v3.1 to v4.0 and study an instance vulnerability.
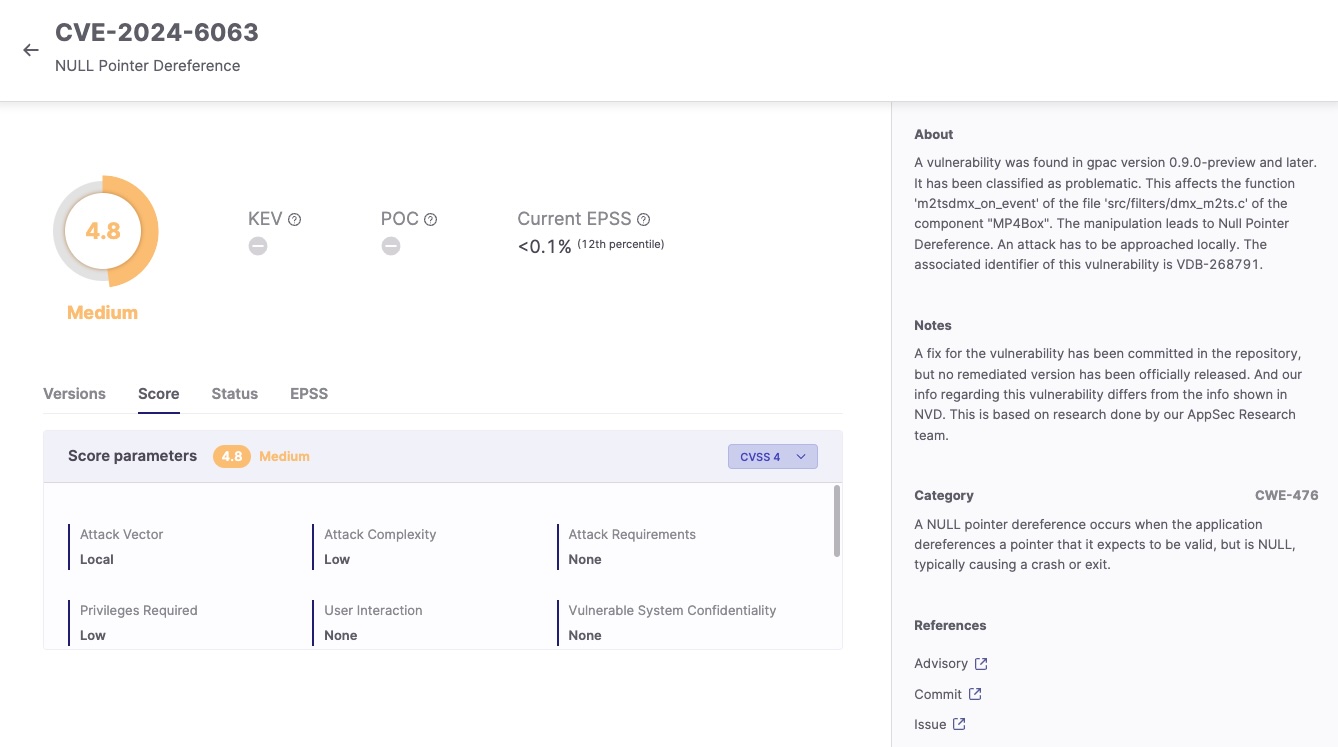
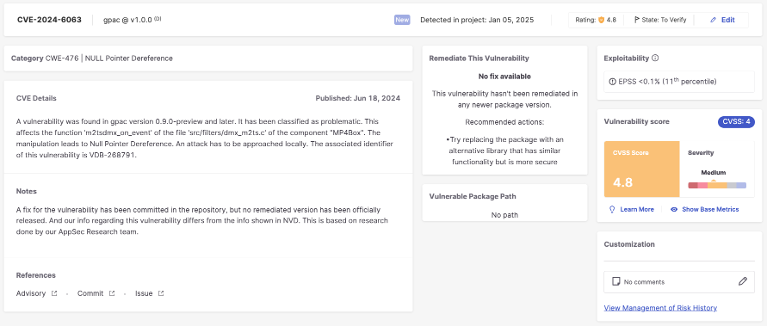
Instance – CVE-2024-6387
CVE-2024-6387 is a vulnerability affecting OpenSSH’s server (sshd), often known as regreSSHion. The vulnerability arises from a default configuration for the sign handler. By exploiting a race situation on this default conduct, an unauthenticated attacker would possibly have the ability to achieve root entry to the server and execute instructions.
Key traits of this vulnerability:
- Assault Necessities are Current as a result of an attacker must win a race situation.
- Assault Complexity is Low in a normal state of affairs since no mitigative measures are concerned.
- No Person Interplay is required.
- Scope is Unchanged in model 3.1, subsequently there is no such thing as a Subsequent system impression in model 4.0.
- Confidentiality, Integrity, and Availability are absolutely impacted for the reason that attacker can execute instructions with full privileges.
Ensuing scores:
- CVSS v4.0: 9.2 (Essential)
The rating change displays the improved granularity and context-awareness of CVSS v4.0. When evaluating this vulnerability in a selected context with extra parameters (e.g., ASLR measures, menace intelligence), the rating might be additional refined to higher replicate the real-world severity.
Supplier vs. Client Roles
CVSS v4.0 introduces a clearer distinction between metrics which might be anticipated to be crammed by the vulnerability supplier (corresponding to software program distributors or safety researchers) and those who needs to be assessed by the buyer (people or organizations utilizing the affected software program):
Supplier Position
Suppliers use their intimate software program data to evaluate Base Metrics, together with assault vector, complexity, and potential impression. They supply the muse for vulnerability evaluation based mostly on their experience with the affected software program.
Client Position
Shoppers play a significant function in contextualizing vulnerabilities inside their particular environments. They need to present the Menace metrics through the use of their very own menace intelligence sources, in addition to precisely assess the Environmental Metrics, which have in mind components just like the significance of affected belongings and any safety measures in place.
This distinction permits for a extra complete and correct vulnerability evaluation, combining the technical experience of suppliers with the contextual data of client.
Transition to Model 4
The adoption of CVSS v4.0 will likely be a gradual course of requiring updates to instruments, processes, and workforce data. Key steps within the transition embrace:
- Updating vulnerability administration instruments to help CVSS v4.0 metrics and scoring
- Refreshing vulnerability administration processes and prioritization methods
- Integrating menace intelligence feeds into vulnerability administration processes
- Investing in coaching for safety professionals to grasp new ideas and metrics
- Integrating asset administration information with vulnerability scanning outcomes to leverage Environmental metrics
Conclusion
Whereas the transition to CVSS v4.0 could require effort, the improved accuracy and suppleness it presents ought to finally result in more practical vulnerability administration and a stronger safety posture. Organizations that spend money on adopting this new model will likely be higher geared up to evaluate and prioritize vulnerabilities of their more and more advanced IT environments.
CVSS 4.0 and Checkmarx
With regards to managing your utility safety posture, having the fitting instruments makes all of the distinction. Checkmarx SCA answer absolutely helps CVSS 4.0, serving to you to higher prioritize and act on the dangers that matter most.