Each developer is aware of the frustration: You’re within the movement, crafting elegant code, when all of the sudden you’re pulled again to repair safety vulnerabilities in work you thought was completed way back. This fixed context-switching isn’t simply annoying; it’s costly and dangerous.
Whereas enterprise builders perceive the significance of utility safety (AppSec), it slows them down. As a substitute of utilizing all their time for creativity, coding, and debugging – their “most important job” – AppSec requires them to spend rising quantities of their time going again to older code and shutting all kinds of safety gaps that safety groups are centered on. The result’s a discount in improvement velocity and progressively rising “safety fatigue.”
As all kinds of cyber-attacks are on the rise, and the widespread adoption of GenAI amongst builders provides much more dangers, it may well really feel like AppSec necessities are on a collision course with developer expertise.
Luckily, improved AppSec know-how is now enabling improvement groups to “shift left,” making it simpler, quicker, and smoother to deal with utility safety dangers as a part of the earliest software program improvement phases: whereas writing code and earlier than committing code to supply code administration methods (SCMs), similar to GitHub.
The Advantages of Shifting Left
When most AppSec dangers are addressed early within the software program improvement lifecycle (SDLC), builders seldom have to return to beforehand written code to shut safety gaps.
This dramatically reduces the price and complexity of remediation duties down the street; it’s well-understood that addressing safety gaps later is harder, takes longer, and should must be carried out below high-stress or emergency circumstances (e.g., following the detection of an precise safety breach).
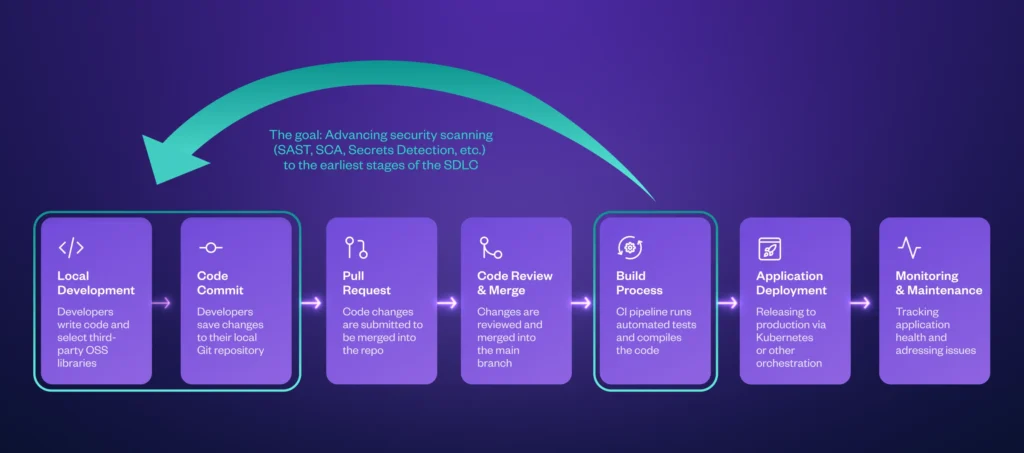
Shifting left: Advancing safety scanning to verify code and dependencies for vulnerabilities (and supply inline remediation steerage to builders) from the Construct stage to the sooner Native Improvement and Code Commit phases improves safety, whereas saving time, rising productiveness, and enhancing developer expertise.
However We Already Scan Our Code at Construct!
Scanning code at construct time or upon pull requests are frequent approaches. Nevertheless, they create a basic timing drawback: Many of those automated safety scans are too late within the SDLC to offer optimum safety. By the point purposes are being compiled and deployed, the phases of writing code and incorporating third-party dependencies are already concluded.
Blocking builds is nice for safety goals, however it delays model launch timelines and doesn’t alleviate a lot of the safety fatigue affecting builders. A greater method is required.
Realtime Code Evaluation and Remediation
Think about if every developer was teamed with an AppSec knowledgeable who watched each line of code being written, and who instantly identified something that might pose a possible safety difficulty. Moreover, think about that this knowledgeable would clarify the chance and supply in-context remediation suggestions on the spot.
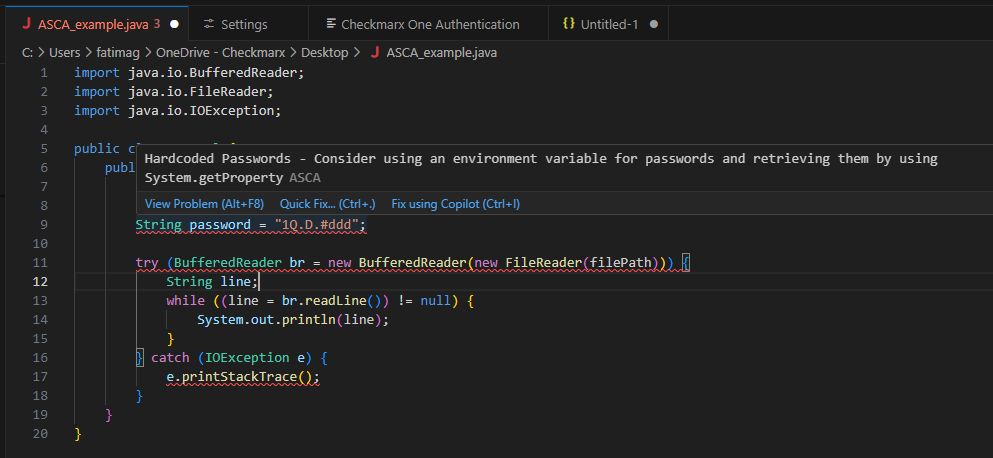
By basically reworking each enterprise developer into an enterprise AppSec knowledgeable, the amount of downstream AppSec alerts is dramatically diminished, enhancing the enterprise’s total utility safety posture and the developer expertise.
That is precisely what realtime code evaluation and remediation know-how does. Combining a number of safety scanning applied sciences embedded inside the developer’s built-in improvement setting (IDE), realtime code evaluation can detect – and counsel in-line remediations for – many safety flaws, together with:
- Weak code, written by builders or generated by AI coding assistants, that may be exploited by attackers
- Incorporation of third-party packages containing susceptible or malicious code, whether or not the references to the packages have been written in-house or generated by AI
- Hardcoded secrets and techniques (e.g., credentials, keys, tokens) that, if contained in shared repositories, can expose a corporation to produce chain assaults
- Misconfigurations in infrastructure as code (IaC) information that may go away a corporation’s setting open to assault
As soon as context-aware detection and remediation help capabilities are an integral a part of the continuing improvement course of, builders can simply perceive and tackle safety points with out pointless friction or lengthy lag occasions.
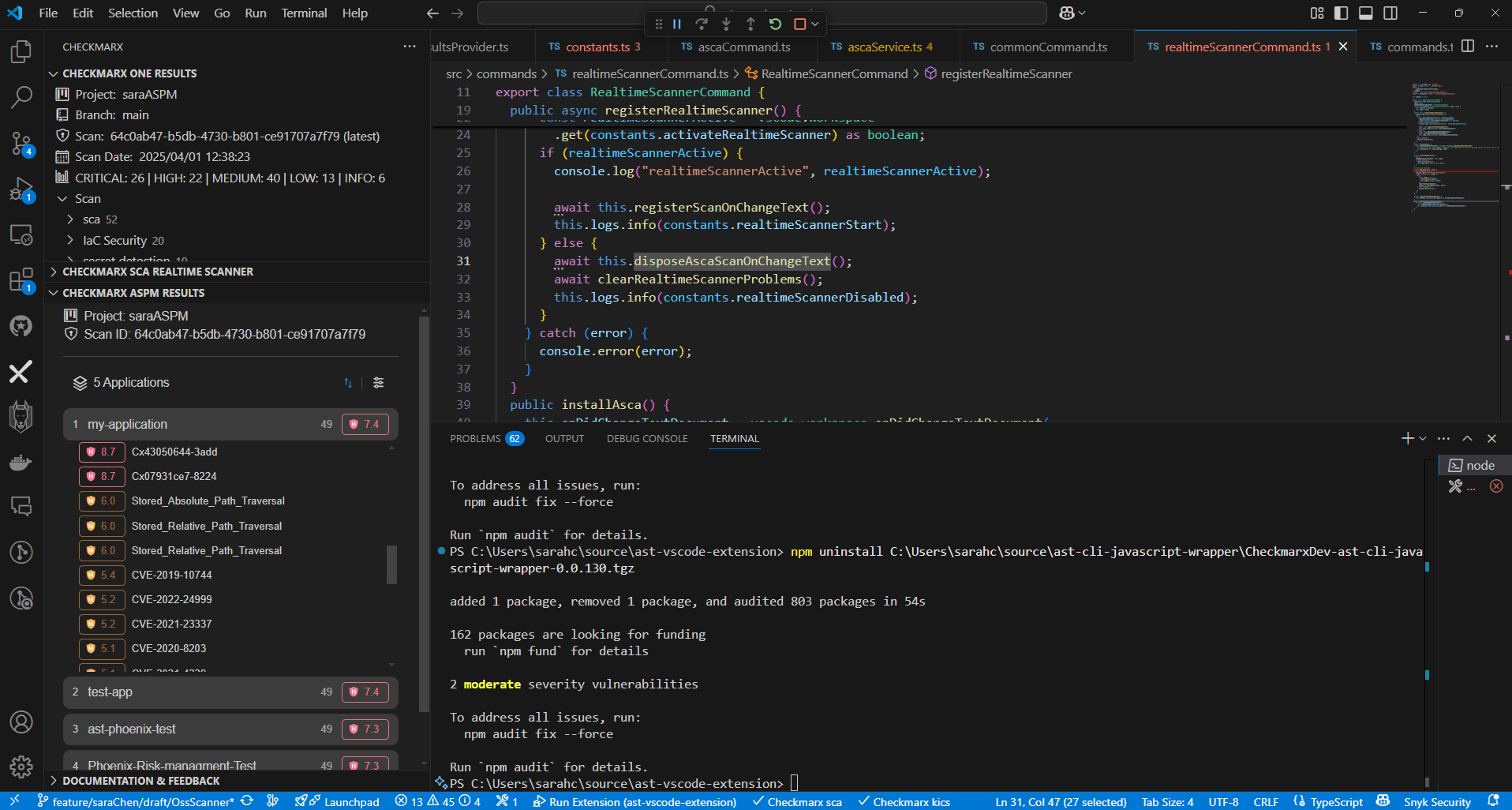
When builders obtain utility safety posture administration (ASPM) reporting contained in the IDE, they will effectively prioritize and tackle probably the most vital vulnerabilities discovered within the code they’re chargeable for – to enhance their code high quality and forestall pointless later work when the identical points are reported by the AppSec group.
Nevertheless, even the very best realtime evaluation depends on developer adoption. That’s the place pre-commit scanning creates an extra security internet.
Pre-commit Code Scanning
Whereas realtime code evaluation and remediation holds the potential to remove most utility safety vulnerabilities, it nonetheless depends on builders selecting to make use of those applied sciences. If a developer feels below an excessive amount of time stress, for instance, to deal with each in-line alert generated by such a instrument, these alerts will go unheeded, and the software program will nonetheless find yourself containing vulnerabilities.
Because of this, it is usually necessary for enterprise improvement organizations to implement automated pre-commit code scanning. Utilizing “hooks” (instructions or scripts which are routinely executed earlier than a Git “commit” is carried out), all code may be scanned for quite a lot of risks earlier than it ever reaches the SCM or different code repo.
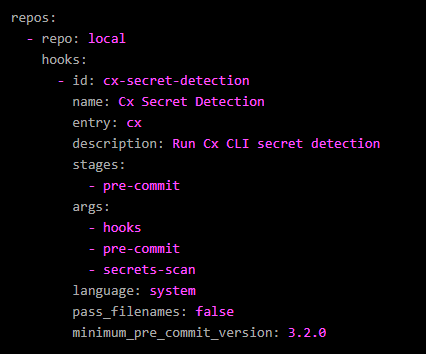
Defining “hooks” permits the automated scanning of code for quite a lot of risks earlier than “commits” in order that dangerous code by no means reaches code repository.
Since builders usually commit code modifications quickly after engaged on the code, receiving a listing of dangers to deal with at this level continues to be way more handy than getting them at some later time limit. And, in fact, stopping dangerous code and hardcoded secrets and techniques from ever reaching code repositories ends in safer compiled purposes, much less publicity to breaches, and a considerably decrease risk-remediation burden for builders later.
Organizations ought to routinely run the next kinds of code scans previous to allowing code commits from finishing:
- Static utility safety testing (SAST) – to restrict the presence of exploitable code vulnerabilities in compiled purposes
- Software program composition evaluation (SCA) – to stop the deployment of susceptible third-party libraries or the violation of third-party code licenses, and to make sure the fixed availability of up-to-date software program payments of supplies (SBOMs)
- Malicious package deal safety (MPP) – to stop third-party libraries containing malware from reaching code repositories, artifact registries, or operating purposes
- Secrets and techniques detection – to stop the attainable publicity of delicate credentials to unauthorized events who could attempt to exploit them
- Infrastructure as code (IaC) scanning – to make sure that there aren’t any misconfigurations that may endanger the group’s software program infrastructure
Organizations have to create insurance policies round these scans to steadiness safety wants with developer expertise and productiveness. For instance, most builders will settle for cancelation of a code commit if the code comprises hardcoded credentials, malware, or third-party code that violates licensing necessities. However, it’s affordable to permit sure kinds of low-severity vulnerabilities to cross by way of within the curiosity of developer velocity and assembly enterprise deadlines.
Due to this fact, any pre-commit code scanning implementation should enable managers to customise the insurance policies in place, to simply fine-tune these insurance policies over time, and to permit related managers to override restrictions on a case-by-case foundation. With out this stage of management – and some of these launch valves – a developer insurrection could happen!
The Essential Significance of Accuracy
A key success think about shifting AppSec left is the accuracy of the applied sciences being applied. If builders are bombarded with “false positives” throughout coding, they are going to rapidly cease trusting (and utilizing) these instruments. Likewise, if their code commits are regularly blocked for “no good motive,” frustration will mount, and developer cooperation with safety groups is prone to undergo.
Attaining low false optimistic charges requires a mix of technological and data-collection capabilities that may be certain that a really excessive proportion of alerts (and urged remediation steps) are right. Some examples of those capabilities embrace:
- Positive-tuned SAST vulnerability detection algorithms that help a variety of coding languages with high-fidelity outcomes
- Remediation steerage able to pinpointing particular person repair places that may tackle a number of vulnerability findings in a single edit
- Efficient SCA reachability evaluation that makes use of multilingual “exploitable path” methodologies to find out which unsafe library features may very well be referred to as at runtime – and that are unused (and thus secure) for now
- Complete and up-to-date databases of third-party code libraries containing susceptible or malicious code – and the very best options, in the event that they exist
- Subtle secrets and techniques detection algorithms that don’t confuse innocent code with delicate credentials, and that may be custom-made when obligatory
- Reside validation of found secrets and techniques to find out if they’re nonetheless exploitable
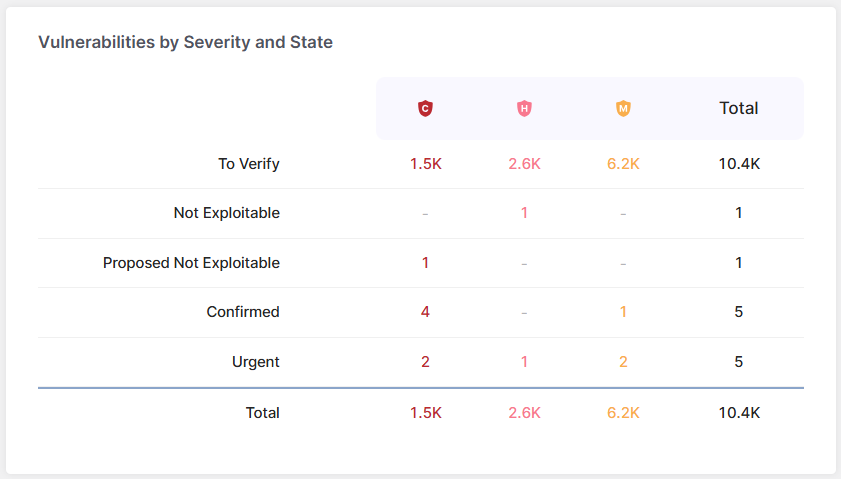
Having an correct high-level view of the general utility safety posture always helps groups to prioritize the fixes that matter most.
This Shift is Already Taking place
The confluence of a number of developments is quickly accelerating the adoption of realtime code evaluation and computerized pre-commit safety scanning in enterprise software program improvement environments. These embrace:
- The bigger assault floor offered by fashionable software program provide chains
- The ever-increasing quantity and class of cyber-attacks
- The sudden ubiquity of AI-driven code-generators
- The better consideration being paid to developer expertise by safety professionals
- The emergence of recent applied sciences to raised (and earlier) detect (and assist remediate) software program safety points
This proactive shift towards early threat detection and remediation is revolutionizing the connection between enterprise improvement and safety groups, with great advantages: increased ranges of utility safety together with improved developer expertise. By automating embedded AppSec scanning – and remediation steerage – the place builders dwell, each safety and productiveness soar.
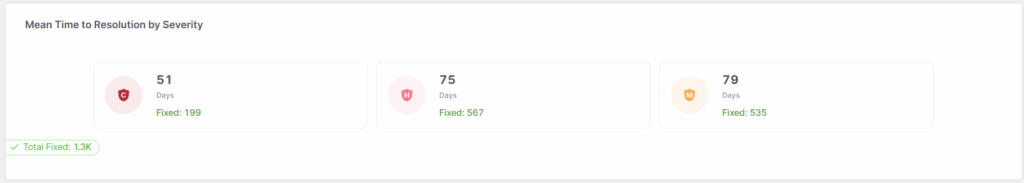
Steady visibility and measurement of developer productiveness and the power to deal with high-risk vulnerabilities are key elements of efficiently shifting left in AppSec.
Able to Remodel Your AppSec Method?
So, how will you begin shifting your AppSec additional to the left, whereas enhancing each utility safety posture and developer productiveness? Listed here are some urged subsequent steps to get you began:
- Assess your present safety posture – Establish the place vulnerabilities are usually present in your SDLC and calculate remediation prices.
- Choose IDE-integrated safety instruments – Consider and implement realtime code evaluation instruments that match your know-how stack.
- Configure pre-commit safety hooks – Arrange automated scanning for vulnerabilities, secrets and techniques, and dependency dangers earlier than code reaches repositories.
- Outline clear safety insurance policies – Set up which points block commits and which generate warnings, balancing safety with developer productiveness.
- Begin with a pilot group – Implement with a small, receptive improvement group to collect suggestions and show worth.
- Put money into developer coaching – Guarantee groups perceive safety dangers and find out how to use the brand new tooling successfully.
- Optimize false optimistic charges – Repeatedly tune detection algorithms based mostly on suggestions to take care of developer belief.
- Measure and talk wins – Observe metrics like vulnerabilities prevented and time saved to show ROI.
- Combine with present workflows – Join new safety instruments with CI/CD pipelines and ticketing methods.
- Scale progressively throughout groups – Roll out to the broader group based mostly on classes realized from early adopters.
By following these steps, you possibly can obtain the twin advantages of improved utility safety and enhanced developer expertise. The journey to shift-left safety is an evolution, not a revolution, however the rewards are properly definitely worth the funding.
Discover how Checkmarx One helps safe code earlier, scale back developer friction, and scale safety throughout your SDLC. Be taught extra right here.


