The Apache Software program Basis has disclosed a high-severity vulnerability in Apache Tomcat that would let attackers exploit improperly dealt with Precedence headers in HTTP/2 to trigger a denial of service (DoS).
Tracked as CVE-2025-31650, this flaw stems from improper enter validation, particularly when the server handles malformed Precedence headers in HTTP/2, leading to reminiscence leaks and potential OutOfMemoryExceptions.
Given Tomcat’s widespread use in enterprise Java deployments, the affect of this vulnerability is far-reaching. Directors and safety groups ought to deal with this as a precedence, particularly since no authentication is required to take advantage of the flaw—making it ripe for automated exploitation.
CVE-2025-31650 – Threat Evaluation
Severity: HIGH
CVSSv3.1: Base Rating: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Exploit obtainable in public: Sure
Exploit complexity: Low
Apache Tomcat’s HTTP/2 module mishandles malformed HTTP Precedence headers, failing to scrub up reminiscence after rejecting invalid requests. As a substitute of discarding these malformed requests safely, Tomcat fails to correctly launch reminiscence related to failed requests. This incomplete clean-up results in a reminiscence leak. If an attacker sends a big quantity of such requests, the server ultimately runs out of reminiscence and crashes—leading to a denial-of-service situation.
Affected Variations
- Apache Tomcat 9.0.76 – 9.0.102
- Apache Tomcat 10.1.10 – 10.1.39
- Apache Tomcat 11.0.0-M2 – 11.0.5
This assault requires no authentication, that means that any unauthenticated attacker can flood a server with invalid requests and produce it down.
Potential Impacts of CVE-2025-31650
1. Denial of Service (DoS)
Essentially the most direct final result is that the applying turns into unavailable to reputable customers. That is significantly damaging for customer-facing providers or essential enterprise operations.
2. Useful resource Depletion
Repeated reminiscence leaks can exhaust system assets, decelerate efficiency, and trigger different unintended behaviors.
3. Operational & Enterprise Dangers
- Elevated troubleshooting time
- Pressing patching necessities
- Service-level settlement (SLA) violations
- Harm to person belief or popularity
CVE-2025-31650 – Mitigation and Suggestions
The Apache Software program Basis urges customers to improve to fastened variations:
- Apache Tomcat 9.0.104
- Apache Tomcat 10.1.40
- Apache Tomcat 11.0.6
If an improve just isn’t instantly possible:
Why Enter Validation Issues
This vulnerability highlights a traditional case of improper enter validation—a recurring weak point in software program growth.
Failing to validate enter like HTTP headers can result in surprising behaviors comparable to:
- Reminiscence corruption
- Useful resource exhaustion
- Utility crashes
Finest Practices for Enter Validation
- Validate all inputs server-side, even when client-side checks exist.
- Use a whitelist/allowlist method—solely enable identified, anticipated values.
- Implement limits on size, format, and type of enter.
- Canonicalize enter to a normal format previous to validation.
- Conduct common audits to determine edge case vulnerabilities in enter processing.
AppTrana WAAP Protection for CVE-2025-31650
To right away mitigate the Apache Tomcat DoS vulnerability (CVE-2025-31650), the managed safety service group has rolled out a devoted safety rule to dam exploitation makes an attempt focusing on malformed or malicious Precedence headers.
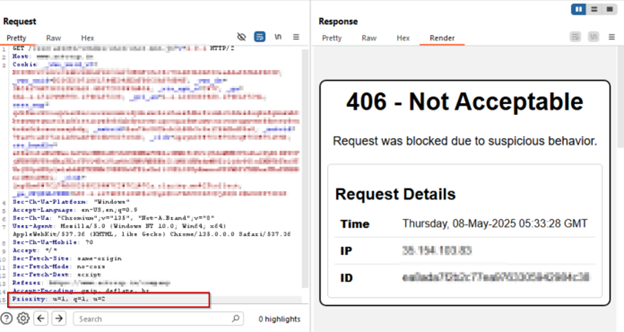
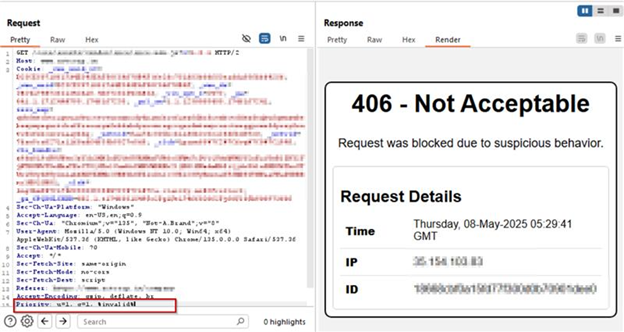
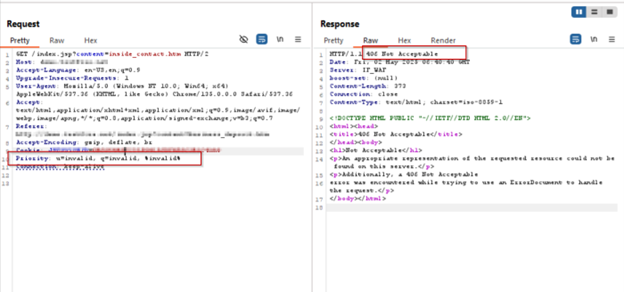
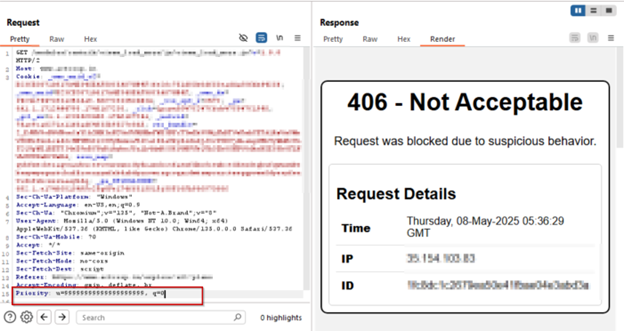
AppTrana WAAP’s customized rule successfully blocked CVE-2025-31650 exploitation makes an attempt throughout proof-of-concept (PoC) simulations, as illustrated within the following screenshots.
Payload 1: u=1, q=1, u=2
Payload 2: u=1, q=1, %invalid%
Payload 3: u=invalid, q=invalid, %invalid%
Payload 4: u=99999999999999999999, q=0
Key Safety Options:
- AI/ML-Based mostly Anomaly Detection: AppTrana makes use of machine studying to determine deviations from regular HTTP conduct, flagging suspicious patterns even when they don’t match a identified signature.
- Behavioral-Based mostly Price Limiting: The WAAP analyzes site visitors conduct over time and dynamically throttles suspicious request spikes—particularly these focusing on HTTP/2 endpoints—with out impacting reputable customers.
- Actual-Time Mitigation: All malicious payloads are intercepted in actual time, stopping reminiscence exhaustion or server instability.
- Zero-Day Protection: The WAAP is repeatedly up to date with new guidelines to fight rising threats—serving to organizations keep safe even in the course of the window between disclosure and patch deployment.
Keep tuned for extra related and fascinating safety articles. Comply with Indusface on Fb, Twitter, and LinkedIn.



