Software program provide chain safety (SSCS) assaults are on the rise.
Actually, in accordance with Infoworld, “we’re within the midst of a fast surge in software program provide chain assaults,” with a staggering 742% annual enhance, leading to prices exceeding $4 million. Gartner predicted that by 2025, 45% of organizations worldwide can have skilled assaults on their software program provide chains, a three-fold enhance from 2021.
The rising variety of high-profile SSCS assaults and information breaches (comparable to SolarWinds, NotPetya, CCleaner, Goal, Equifax and Kaseya VSA) have elevated consciousness of SSCS vulnerabilities. This alarming pattern emphasizes the necessity for enterprises to allocate extra assets into securing their software program improvement and deployment processes, from code to cloud.
However how did we get right here? Fifteen years in the past, most enterprises completely relied on internally developed code. As we speak, nonetheless, most trendy code bases are largely constructed with open supply packages and third-party code. Whereas this shift accelerates improvement and fosters extra modern code, it additionally introduces extra vulnerabilities – whether or not from human error, careless publicity of secret keys (passwords, encryption keys, and entry tokens), or malicious third-party code. Moreover, the current uptick in AI-generated code from digital assistants like ChatGPT, GitHub Copilot, and Codestral has additional elevated the danger of insecure code discovering its manner into enterprise purposes.
Prefer it or not, trendy improvement requires using third-party codebases, regardless of the dangers they could carry. That’s why enterprises want an answer to successfully handle and mitigate the dangers related to these third-party libraries.
AppSec Has Historically Centered on Internally Developed Code
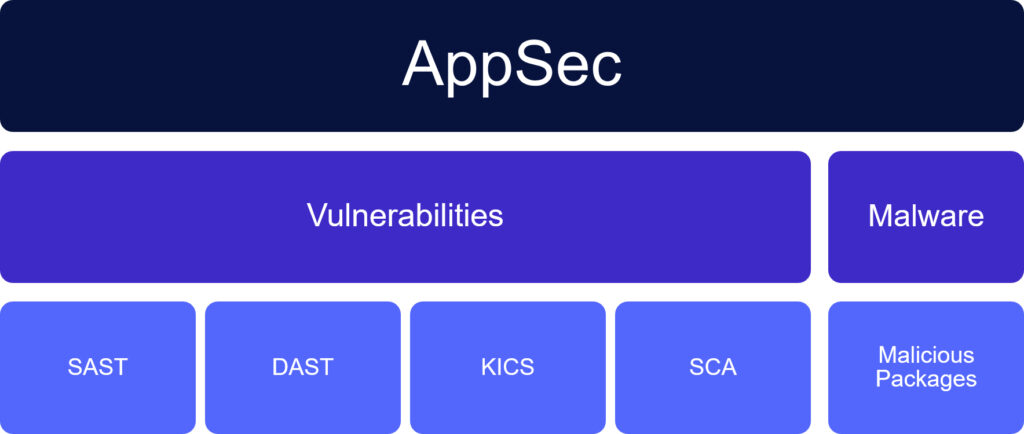
Determine 1 – Conventional utility safety centered solely on discovering vulnerabilities in proprietary code.
Till lately, utility safety (AppSec) primarily centered on the code developed by the enterprise in-house. This made it simpler to detect and remediate safety vulnerabilities, as a result of the code was completely written by their very own builders. Vulnerability detection for these code bases usually relied on static utility safety testing (SAST) and dynamic utility safety testing (DAST).
Actually, when Checkmarx was based 18 years in the past, we additionally centered on this conventional AppSec mannequin, concentrating on securing the code developed internally by enterprises.
Why Software program Provide Chain Safety Now?
What modified? Lately, the significance of securing the software program provide chain from code to cloud has grown steadily amongst enterprise CISOs, AppSec managers, DevOps groups, and builders.
This shift is pushed by 4 key components:
- In depth use of open supply packages and different third-party code
- Migration of purposes to the cloud (cloud-native purposes)
- Incorporation of automated compile/deploy workflows (CI/CD)
- Proliferation of assaults on the software program provide chain
These modifications in trendy improvement have launched larger dangers to software program safety than ever earlier than. Securing purposes now requires involvement from each stage of the software program improvement lifecycle (SDLC), from code to cloud. To deal with these new risk vectors, Checkmarx developed a complete, built-in resolution that protects the complete software program provide chain.
SSCS Begins With SCA and Malicious Package deal Safety
Surveys point out a dramatic enhance in using open supply libraries, with as much as 97% of purposes now incorporating open supply code. This statistic is no surprise, contemplating how open supply libraries considerably pace up improvement and scale back enterprise prices.
Nonetheless, this new, elevated use of open supply code has additionally uncovered enterprises to an enormous new risk vector: each unintentional vulnerabilities and deliberately malicious code – each of which might be exploited.
Checkmarx has tailored to the evolving dangers within the software program provide chain and has turn into a frontrunner in addressing these open supply dangers. How? Our Software program Composition Evaluation (SCA) resolution gives enterprises with a robust safety towards a majority of these malicious packages. Checkmarx’ SCA resolution:
- Comprehensively discovers and itemizes all open supply packages utilized in purposes (together with transitive open supply dependencies)
- Identifies open supply packages containing susceptible code, malicious code, or suspicious conduct (comparable to typosquatting, starjacking, and repojacking)
- Prioritizes remediation efforts utilizing a number of analyses (e.g., reachability/exploitable path evaluation and SAST correlation)
- Gives AppSec groups and builders with particular and actionable remediation steerage
- Integrates with CI/CD and IDE instruments to easily combine safety testing and remediation workflows into current deployment and improvement platforms
- Generates an industry-standard software program invoice of supplies (SBOM)
- Detects authorized and compliance dangers related to open supply licensing points
- Enforces coverage guidelines to robotically ship alerts and forestall builds based mostly on a variety of things
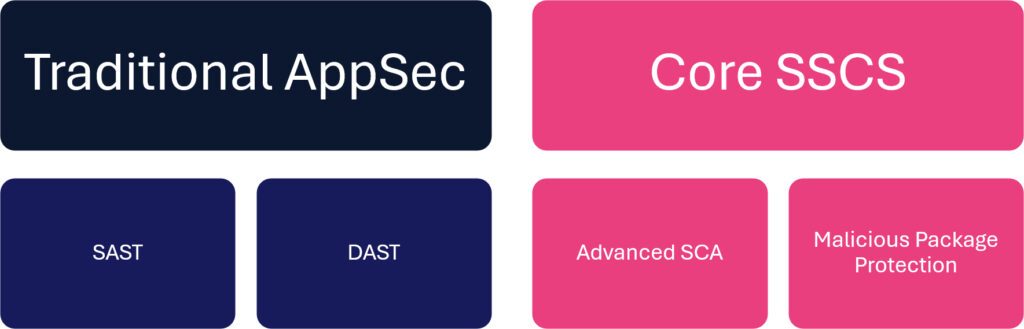
Determine 2 – Step one to increasing utility safety into software program provide chain safety is including superior SCA with malicious bundle safety.
Checkmarx One: Superior AppSec Together with SSCS
Sadly, even superior SCA options are now not sufficient to guard towards SSCS assaults. To completely shield the software program provide chain, Checkmarx now presents a whole suite of industry-leading options to safe each internally developed code and the software program provide chain parts that they devour.
Checkmarx One is a code- to -cloud platform that gives an built-in SSCS resolution that no enterprise can afford to be with out. Along with our SAST, DAST, SCA, and malicious bundle safety capabilities, Checkmarx One covers the complete software program provide chain with the next capabilities:
- Container Safety – Establish and mitigate dangers in container photos, container infrastructure, and runtime code.
- AI Safety – Mechanically scan AI-generated supply code and referenced open supply libraries for susceptible or malicious code.
- IaC Safety – Safe cloud infrastructure with proactive vulnerability identification and misconfiguration detection.
- API Safety – Uncover and remediate each API vulnerability.
- Secrets and techniques Detection – Mechanically uncover the presence of delicate credentials.
- Repository Well being – Get complete well being scorecards for software program repositories.
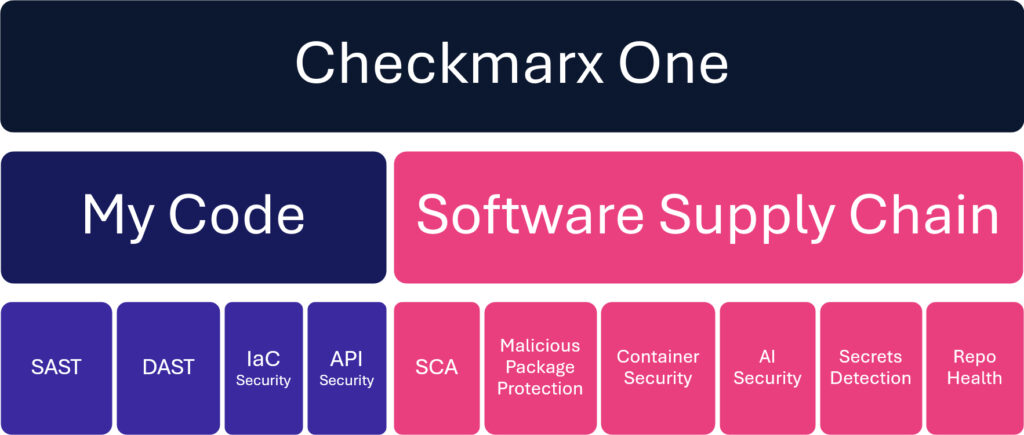
Determine 3 – Checkmarx One delivers complete code-to-cloud utility safety, together with protection for vital software program provide chain risks.
Extra About Our Latest Capabilities
Secrets and techniques Detection and Repository Well being are the latest additions to the Checkmarx One suite aimed toward defending towards software program provide chain dangers. Let’s take a better take a look at these new choices:
Secrets and techniques Detection
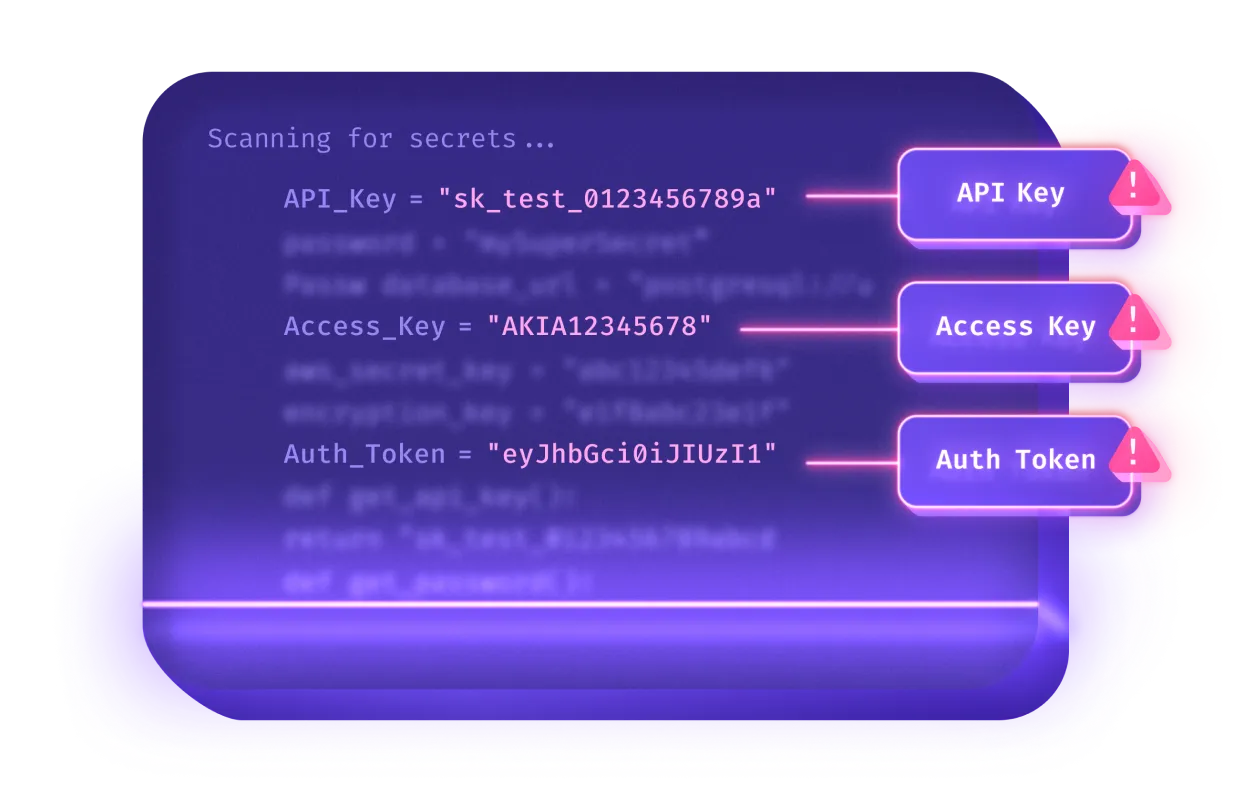
Determine 4 – Secrets and techniques Detection minimizes threat by figuring out delicate credentials which might be vulnerable to being unintentionally uncovered.
Enterprises unintentionally expose hundreds of secret credentials in GitHub and different publicly accessible or insecure areas day by day. This publicity can allow unauthorized entry to your techniques, doubtlessly leading to cyber-attacks, monetary loss, and reputational harm. As soon as credentials are compromised, attackers can transfer laterally inside techniques to extract information, deploy malware, or launch additional assaults on infrastructure, clients, and companions.
Checkmarx’ Secrets and techniques Detection minimizes threat by shortly figuring out delicate credentials which may be unintentionally uncovered – and pinpoints which of them are nonetheless legitimate. With this perception, your improvement and safety groups can shortly remediate points by eradicating uncovered secrets and techniques and updating them to stop any unauthorized utilization.
Scanning for uncovered secrets and techniques might be initiated on demand or manually with automated triggers by way of SCM integration (e.g., pull request, construct). Found secrets and techniques are robotically validated to find out if they’re nonetheless in impact and thus doubtlessly exploitable.
This gives three key advantages:
- Decrease provide chain threat by stopping the publicity of secret credentials, lowering the possibility of attackers accessing your techniques or stealing information.
- Enhance regulatory compliance by assembly information safety necessities (e.g., GDPR, HIPAA, PCI DSS, SOX, FISMA, CCPA) and avoiding fines and reputational harm.
- Improve developer effectivity by permitting builders to provoke scans, overview found secrets and techniques, and obtain remediation steerage immediately inside their IDE.
Repository Well being

Determine 5 – Repository Well being gives ongoing visibility into the safety and upkeep well being of the code repositories utilized in enterprise purposes.
Enterprises additionally want a dependable solution to repeatedly consider the riskiness of the open supply code used of their purposes, in addition to a way to observe the standard and safety of the repositories containing their internally written code.
Checkmarx’ Repository Well being maximizes the safety posture of your software program provide chain by repeatedly monitoring well being scores for all repositories in your purposes. Scoring is predicated on greater than a dozen key components in areas, comparable to code high quality, dependency administration, CI/CD greatest practices, and challenge upkeep.
Repository Well being can robotically scan repositories upon repository updates, guaranteeing up-to-date repo well being metrics with no handbook effort. Builders and safety groups may also run on-demand repo well being scans at any time by way of API, CLI, or the Checkmarx One UI.
Moreover, repository well being scores are included in Checkmarx One stories, offering visibility into – and environment friendly prioritization of – safety vulnerabilities, code high quality points, and repository well being dangers, multi function place.
The three key advantages this gives embody:
- Decrease provide chain threat – Visibility into the safety well being of open supply parts and your personal code repositories that closes an essential hole in software program provide chain safety.
- Environment friendly holistic threat prioritization – Figuring out and prioritizing high-risk areas throughout the software program provide chain that permits builders and safety groups to focus their efforts on essentially the most vital safety points.
- Enhanced transparency and communication – Clear, quantifiable metrics on the safety posture of open supply dependencies and first-party repositories that enhance transparency and communication amongst stakeholders.
Be taught Extra
Given the wide selection of risk vectors going through enterprise purposes and the software program provide chain, deploying essentially the most complete and efficient safety options is crucial. And these options should additionally domesticate a superb developer expertise to encourage adoption and assist seamless, environment friendly workflows.
Counting on a hodge-podge of various instruments to guard your provide chain is now not viable – it’s costly, inefficient, and tough to take care of. To guard your enterprise from information breaches or different system infiltrations unified platform that covers all of your bases. And that’s the place Checkmarx is available in.
Contact us for a free demo of Checkmarx One and uncover the {industry}’s greatest resolution for securing your enterprise’s purposes and the software program provide chain.


